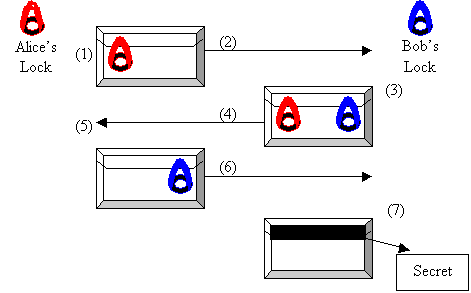
Premium Vector | Concept of private key in cyber security technology, graphic of lock pad combine with binary code and electronic key

Bitcoins digital wallet with lock and private key isolated on white background,3D illustration concept. Stock Illustration | Adobe Stock

Lock Secure Security Password Private Key Comments - Security PNG Image | Transparent PNG Free Download on SeekPNG